Cyber Threat Hunting, 3 steps to anticipate the unknown.
Follow these 3 steps to anticipate the unknown
Use Cyber Threat Hunting to anticipate the unknown
Faced with the omnipresence and interconnection of information systems on the one hand, and the increase and sophistication of threats on the other, cybersecurity has become a vital necessity. Maintaining strong security is an increasingly complex responsibility.
Data breaches and cyberattacks cost organizations millions of euros a year and Cyber Security teams face high rates of data growth and an ever-growing attack surface with new applications and services constantly being added (with or without approval).
Establishing a cybersecurity program takes hard work and organizational support and there is no one-size-fits-all solution. Manpower alone is not enough to cope with the ever-increasing volume of cyber threats. Security teams need a relevant force multiplier to help maximize the use of their human and financial resources.
In an effort to build and support a comprehensive and mature cybersecurity program, many organizations have assembled a heavy cyber security arsenal and implemented an astounding technological advancement. While intentions were sound, logic was sometimes lost, resulting in excessive expenses and clutter.
No cybersecurity protection is forever 100% effective. Most automated network and endpoint security controls use signature-based and rule-based alerts for IOCs, which only detect “known items,” such as malware hashes. A cyber threat could be lurking in any corner of an organization’s infrastructure and every time the defender invents a way to ward off a threat, malicious actors look for ways around it.
If we stop, zoom out, and think pragmatically about what a security team is intended to do, the answer is fairly simple: enable business while reducing risk by understanding exposure and in fine such understanding ultimately allows us to prioritize exploitable vulnerabilities over theoretical ones and maximize risk mitigation.
To combat this, threat hunting is nowadays an essential component of any cybersecurity strategy. For many SOCs, that’s the rationale for building a threat hunting program.
What’s Cyber Threat Hunting?
Threat hunting is identifying and sneaking up on an enemy that’s already inside your perimeter when they aren’t expecting it. It aims to always better identify and better anticipate hacking techniques. It consists in searching iteratively through networks and detect indicators of compromise (IoCs), hacker tactics, techniques, and procedures (TTPs), and threats such as Advanced Persistent Threats (APTs) evading your existing security system.
As the saying goes, the best form of defense is attack. Threat hunting techniques shift enterprises from reactive response to proactive identification, enabling them to get ahead in the fight against adversaries.
Threat hunting can reduce the risk and impact of threats while improving defenses against new attacks. The top benefit of threat hunting is a better detection of advanced threats.
Whether the information is about benign or malicious activity, it can be of use for future analysis and investigations. You can leverage the gathered information to predict trends, prioritize and remediate vulnerabilities, and improve your security measures. Any reduction in dwell time minimizes potential loss.
Unfortunately, while many organizations understand the need to adopt threat hunting practices, it’s not an easy task to undertake.
Before you go hunting or do anything to address cybersecurity concerns, take some time to learn about threats and those which are most likely to target your organization and industry.
You must understand the cyber adversaries you’re facing, first. If you can determine who would want to do you harm and what you have that’s valuable to them, you can better protect your business.
To successfully hunt for threats, you need to understand how a typical attack unfolds. Just keep in mind that hackers can skip steps, add steps, and even backtrack.
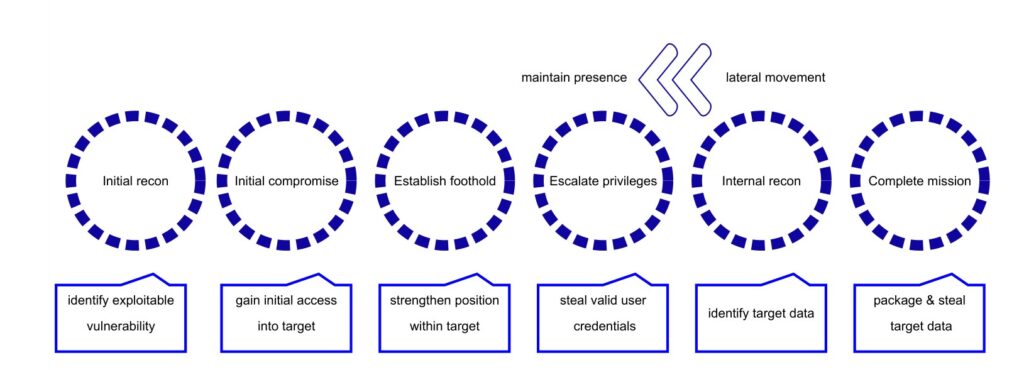
Cyber Attack Lifecycle
Recommended Actions:
You need to determine adversary intent like financial gain and identify your most sensitive asset in your organization such as sensitive customer or data and intellectual property that might appeal to threat actors.
You may consider threat actors capability and target the suspect list based on intent, so you can do your own reconnaissance into Tactics, Techniques and Procedures.
To prioritize tasks, the concept of ease of detection vs. difficulty caused for the adversary can also be used. It is represented in the Pyramid of Pain (POP), as defined by David Bianco.
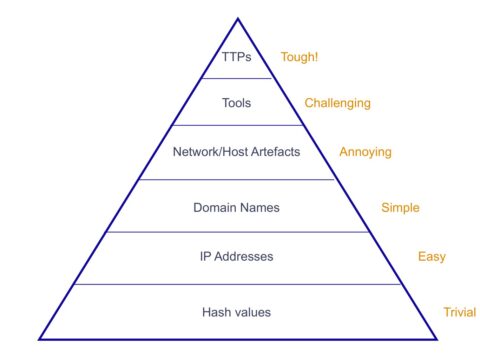
Pyramid of Pain (David Bianco)
At last, you need to assess attacker opportunities created by work from home, collaboration tools, use of mobile devices, increased reliance on cloud-based applications and internet connected devices.
Threat hunting is playing offense. Why wait for someone to tell you that your organization has been attacked or breached? A good place to start to understand how to protect your organization from cyber threats is with the National Institute of Standards and Technology’s (NIST) Cybersecurity Framework (NIST Cybersecurity Framework) and a cyber threat intelligence exercise.
Architecture is a good starting point. Inventory the assets in your enterprise, plan, implement and update systems with security in mind – but be sure to balance technology with people and processes.
Operate on the assumption that there are no silver bullets, even if you have defense in depth with next-generation firewalls, antivirus software, intrusion detection systems and Zero Trust security.
Recommended Actions:
We recommend to add passive defense with systems that reduce human interaction and build from there.
You must establish comprehensive visibility by monitoring gateways, networks and endpoints.
Missing data can lead to a missed cyber threat. Begin collecting data from your assets and establish active defense by adding analysts or a MSSP to monitor, respond to and learn from adversaries within the network.
Maximizing network transparency and analyzing logs of all network devices is essential for the threat hunter. A process is required to aggregate, correlate, and normalize logs, then perform contextual and behavioral analysis in order to detect advanced threats. This is not possible without 24/7/365 managed detection and response (MDR) tools for proactive threat hunting that uses event monitoring logs, automated use case data, contextual analysis, incident alerting and response and applying tactics, techniques, and procedures (TTPs) to identify issues that improve an enterprise’s security posture.
Provide threat hunters with the actionable Cyber Threat Intelligence they require to generate relevant and testable hypotheses. Start leveraging Cyber Threat Intelligence by integrating data from multiple sources. This includes integrating proprietary, third-party, and open-source intelligence, feeds in a single threat hunting platform and automatically enriching hunts with relevant context. The cyber threat hunting process for campaigns like advanced persistent threats, or APTs, is difficult in the absence of threat intelligence. Threat hunters tap into high confidence, high fidelity threat intelligence feeds curated by practitioners and indicators of compromise (IoCs) to inform their analyses.
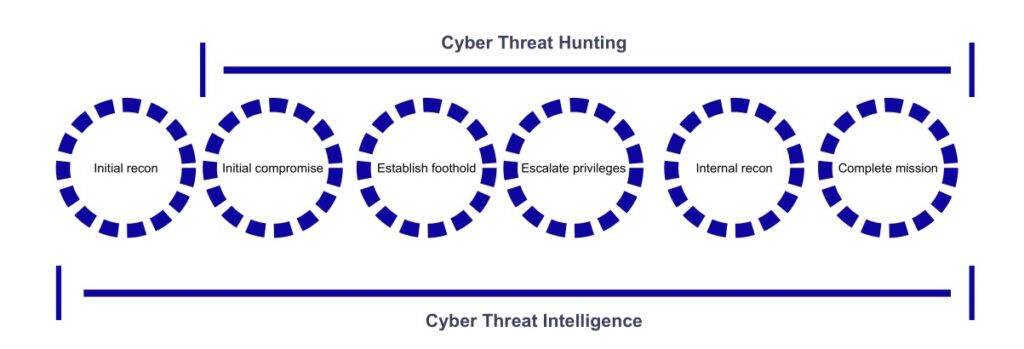
Capability scope comparison
The only way to ensure the best security posture possible is to embrace a combination of defensive and offensive tactics to deter cyber criminals; in other words, use human and artificial intelligence and start hunting.
The Hunter Or The Hunted? That’s the question.
Threat Hunting begins with hunters asking questions, such as “How would a threat actor infiltrate our network?” These questions then need to be broken down into specific and measurable hypotheses that state what threats may be present in the network and how they can be identified. Hypotheses cannot be generated by tools, and instead must be derived from the hunter’s observations based upon Cyber Threat Intelligence, situational awareness, or domain expertise.
Recommended Actions:
Most IT and security teams are already stretched thin, so it can be difficult to effectively focus on hunting. Whether it’s a part-time resource, a dedicated person, or a team, don’t let threat hunters get sidelined by alert response, network maintenance, or vulnerability remediation tasks. Empower them to act against the threat.
Establish a threat hunting baseline through network analysis. Useful tools include endpoint detection and response technology with machine learning and forensics capabilities and a SIEM for correlation and analysis of security alerts. Periodically assess the relevance of automated analytics to the organization.
Utilize a workflow management tool to prioritize and track workload and a central repository to share knowledge and lessons learnt.
One example of a workflow management view is that of Epics and Stories. Epics are bodies of work that can be broken down into specific tasks, which are the Stories. The use of these concepts helps structure workloads, and progress can then be tracked via the use of a Kanban board for each Story type. In the context of Threat Hunting, each Epic could be a tactic from MITRE’s Adversarial Tactics, Techniques and Common Knowledge (ATT&CK™) for Enterprise, with Story types of hypotheses and associated hunts. Individual hypothesis stories can then be tracked through a hypothesis Kanban with example stages such as: Ideas, for basic hypothesis ideas; To do, for adding detail and assessing the scope and dependencies; Doing, for hypotheses ready for testing; and Done, for hypotheses that are no longer relevant.
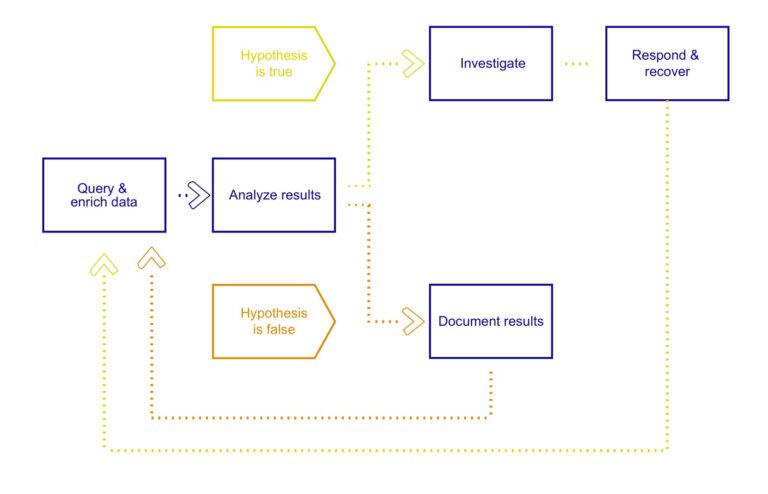
Agile search
Keep hunters focused on answering these questions:
- Why?
- What am I looking at?
- What am I hunting for?
- What is the true threat?
- What is the outcome?
Threat Hunters often spend a lot of time sorting through immense amounts of data in order to spot anomalous behavior. As such, much of Threat Hunting becomes about avoiding rabbit holes. Something can often appear out of place when in actuality it’s not, so Threat Hunters must be able to quickly determine if it is a lead worth pursuing.
So, what happens when a threat is discovered? Well, first things first: Hunters need to check, double-check, and triple-check that the threat is real. Threat Hunters spend most of their time discovering the risk of a potential compromise, but in the case of uncovering an actual compromise, the next step is to immediately initiate an approved security incident response procedure or potentially call in a response team.
Work up an incident response plan, including who does what and when, so you’re ready when you find a true threat.
Engage with a security services provider to share information and close people process and technology gaps. Take advantage of partnerships to offset the chronic shortage of cybersecurity skills and technology debt.
Ahead of the game
Threat hunting is currently a relevant response to the increasing number of attacks. Effective Threat Hunting is based on several key principles: adopt the hacker’s point of view, give teams time to think, give them access to the tools and data they need to understand analyze and detect the intrusion, and finally, react quickly with an appropriate response.
That’s how to stay one step ahead of cyber criminals. Organizations must no longer wait to be alerted of data breach before taking action; today it is essential to have a complete picture of the entire network in real-time, so that unusual activity can be identified and halted immediately, before any damage occurs. With strong Managed Detection and Response tools at the core, security leaders can ensure a strong and effective security posture based on anticipating the unknown, clear visibility into vulnerabilities that pose the biggest threat and identifying barriers that prevent successful tracking and remediation.
Want to learn more? We can help.
Cybersecurity products alone are not enough to protect today’s digital enterprise. That’s why Stroople’s Cyber Threat Hunting offer uniquely combines automated analysis with behavioral playbooks. Designed by our Stroople Lab, it identifies advanced persistent threats and reduces the risk of a missed attack.
Stroople is an independent managed security services provider (MSSP) that is revolutionizing the cybersecurity experience by taking a customized and people first approach. We offer comprehensive services that combine cutting-edge threat detection with cyber security experts.
Need help unlocking your digital potential and protect your most sensitive digital assets ?