Many phishing email are designed poorly with bad grammar, etc. but others look legitimate enough for someone to click if they weren’t paying close attention. Cybercriminals are constantly updating their phishing techniques but there are a few consistent patterns in phishing emails, and if you can learn to identify them, you are much less at risk of clicking on one.
Set up your email software correctly
- update your software, if possible by activating the automatic update procedure;
- set your email program to disable automatic email previews;
- in the security settings in options, prohibit the automatic execution of ActiveX and plug-ins and downloads, either by disabling them or by requiring you to ask for permission;
- in a sensitive environment, read all messages in plain text format.
Set up two-factor authentication (2FA)
2FA is the most effective method for countering phishing attacks, as it adds an extra verification layer when logging in to sensitive applications. 2FA relies on users having two things: something they know, such as a password and user name, and something they have, such as their smartphones. Even when employees are compromised, 2FA prevents the use of their compromised credentials, since these alone are insufficient to gain entry.
Inspect the email sender address
Scammers will pretend to be a company you may know. However, the sender address will be different. For example, instead of laposte.fr they could be using lap0ste.fr or laposte.offre.fr.
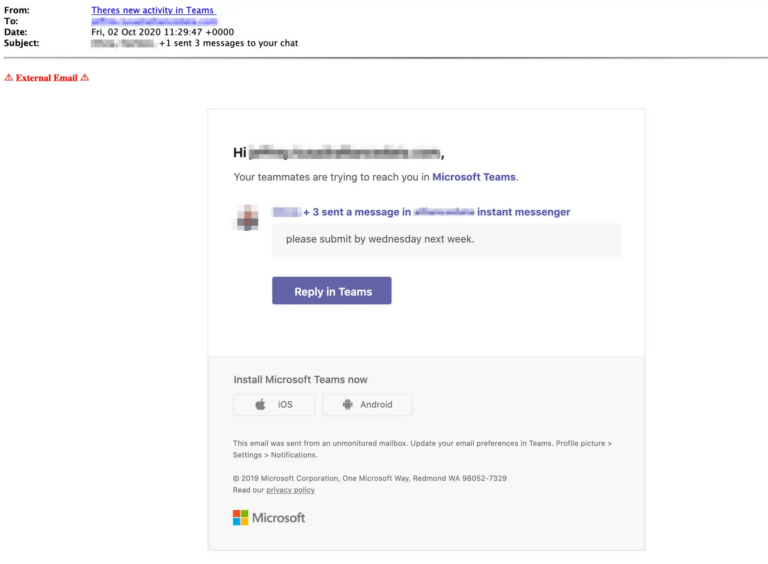
Hover over the link
If the email seems to be coming from a trusted source, hover over the link and verify that the domain matches who it should be. Indeed, when you hover over a link in Outlook or a web browser, a small window pops up to show you where the link really goes. If the real link doesn’t match the sender or doesn’t match what you expect, assume it is poisoned and don’t click it.
Don’t open suspicious attachments
Unexpected or suspicious email attachments should never be opened. These documents too often get past antivirus programs with no problem and they may execute a disguised program (malware, adware, spyware, virus, etc.) that could damage or steal your data. If in doubt, call the sender to verify.
When in doubt, close it out
If you’re not sure what to do with a suspicious email, the best thing is to just delete it. Consult with your manager or security IT staff to inquire about its validity.
Pour aller plus loin ...
Lancer des campagnes anti-phishing
Il existe un certain nombre de techniques différentes utilisées pour obtenir des informations personnelles des utilisateurs. Les techniques utilisées par les pirates informatiques sont de plus en plus sophistiquées à mesure que la technologie progresse.
On pense souvent, à tort, que le phishing est facile à repérer et que seules les personnes peu compétentes sur le plan technique en sont victimes, mais c'est loin d'être le cas. Un test de phishing présente le double avantage de mesurer le risque pour votre entreprise et de former vos employés sur ce qu'il faut rechercher dans ces attaques. Test de sécurité contre le phishing familiariser les employés avec les cybermenaces afin de créer une ligne de défense et de favoriser un environnement plus sûr. Afin de lutter contre ces menaces, le personnel doit comprendre les signes révélateurs d'une attaque, les techniques courantes utilisées par les criminels et ce qu'il faut faire lorsqu'il pense avoir reçu un hameçonnage.