Vulnerability Operation Center
Stay on top of vulnerabilities to patch them before attackers exploit them.
Stay on top of vulnerabilities to patch them before attackers exploit them.
No organization can instantly patch all vulnerabilities. Thousands of new vulnerabilities are disclosed every year, leaving in-house teams struggling to provide corrective patches quickly. Hackers are taking advantage of this lead time to analyse information systems, find vulnerabilities and launch successful attacks.
To support businesses implementing an efficient and cost effective risk-based vulnerability management approach, Stroople has developed a turnkey Vulnerability Operation Center.

The Stroople’s Managed Security Services specialized in Vulnerability Management ensures you have experienced analysts armed with advanced technologies on hand to identify, classify, prioritise and address potential vulnerabilities before they are exploited.
Don’t sit and wait for an attack.
Manage the entire vulnerability management cycle for all your businesses from a single hub.
Thanks to our services, you can clearly see where you’re most vulnerable and how cyber risk affects your business.
Our service is really flexible. If you already have your scanning platform in place you can keep it. If you don’t have any scanning platform in place we will use our scanning platform.
We can also combine both your scanning platform and ours.
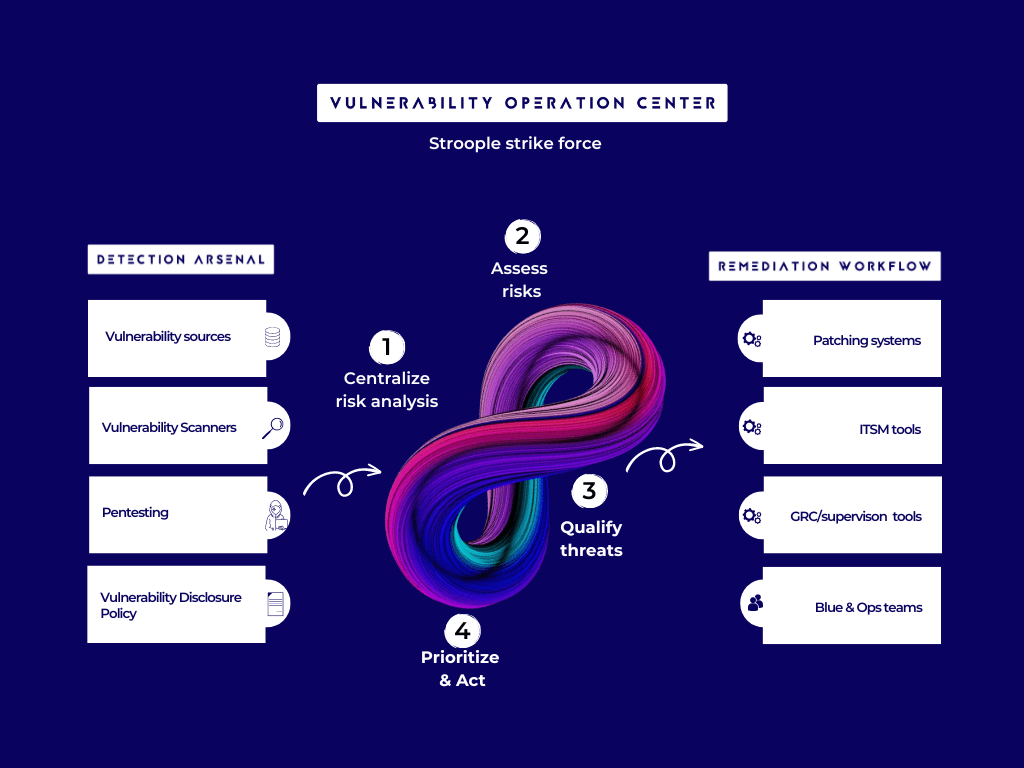
We help you to have a complete asset view, to know where you’re most vulnerable and understand how cyber risk affects your business.
Whether it is network infrastructure, web applications or endpoints, we extract an accurate view of your vulnerability and associated risk data.
Once you have all the data and the ability to visualize it in a way that reflects your true business risk, our experts give you guidance and advice to produce smart, risk-based remediation decisions.
Identifying potential threats, whether it is inside an attack surface or adjacent to it is an essential step.
Round-the-Clock Protection : regularly assess your business’s networks, applications and systems to pinpoint vulnerabilities and weaknesses that attackers could exploit.
Simplicity : have a comprehensive and consolidated visibility for security vulnerabilities.
Scalability : quickly scale up with an already skilled staff.
Agility : have a cybersecurity service that adapts as your needs evolves. This means that your business can easily add or remove services, solutions and capabilities as needed.
