ChatGPT and Cybersecurity: Utilizing AI to Enhance Your Workflow
ChatGPT: The AI ally in your cybersecurity fight
In today’s digital age, cybersecurity is an essential aspect of any organization. As cyber threats become more sophisticated and frequent, it is crucial to have the right tools and strategies in place to protect against them. One such tool is Artificial Intelligence (AI), and ChatGPT is one of the most promising AI-based cybersecurity solutions available today.
We will explore together how ChatGPT can be utilized to enhance your workflow in the case of Governance, Risk, and Compliance (GRC), as blue team and as red team.
Efficiency Boost in GRC with ChatGPT
Governance, Risk, and Compliance (GRC) is a regal and important aspect of any organization’s cybersecurity strategy. All of this activities aim to ensure the organization is secure and compliant with regulations and standards. However, managing GRC may be complex but mainly time-consuming tasks, especially for organizations a lack of expertise.
In this part, we will explore how ChatGPT can assist organizations in their GRC activities. By automating many of the tedious and time-consuming tasks associated with GRC, ChatGPT can help organizations improve efficiency and effectiveness, while also reducing the risk of non-compliance.
Let’s work together to create key messages for a cyber security awareness campaign using ChatGPT
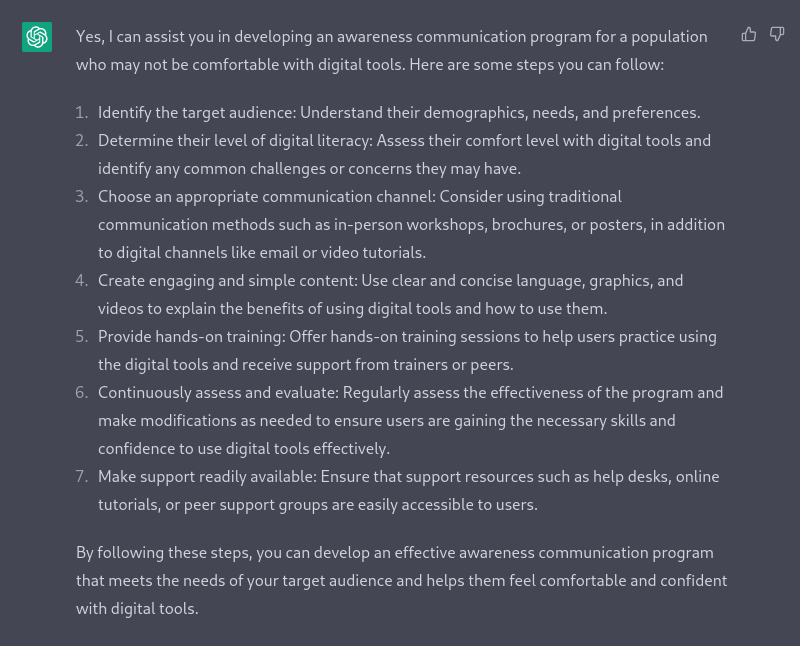
As a GRC consultant, can you assist me in developing an awareness communication program that target a population of users who may not be comfortable with digital tools ?
Why don’t we request ChatGPT, as a GRC consultant, to carry out an up-to-date assessment of the cyber threat in the energy sector:
As a GRC consultant, can you identify the main cyber threats in the energy sector ?

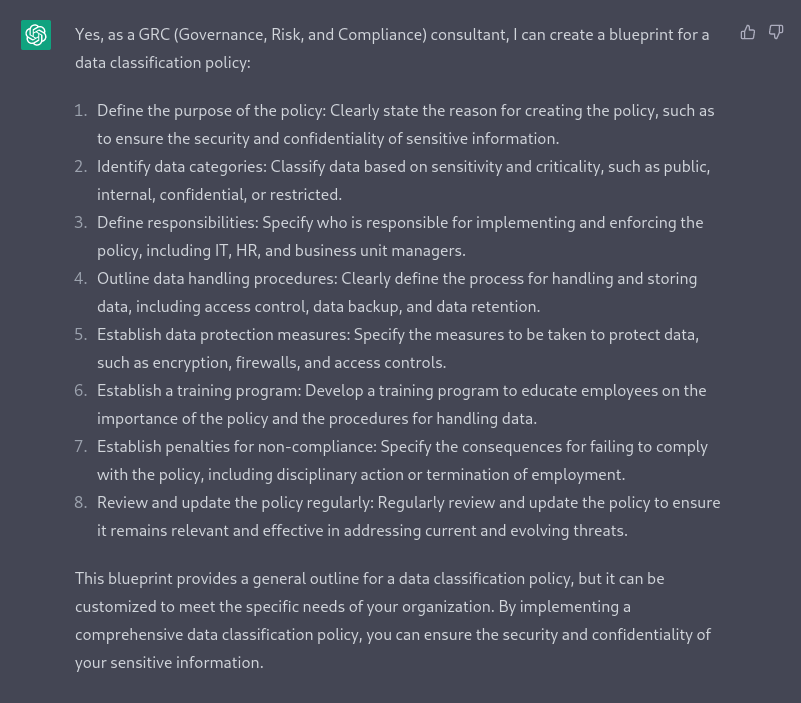
As a GRC consultant, can you create a data classification policy blue print ?
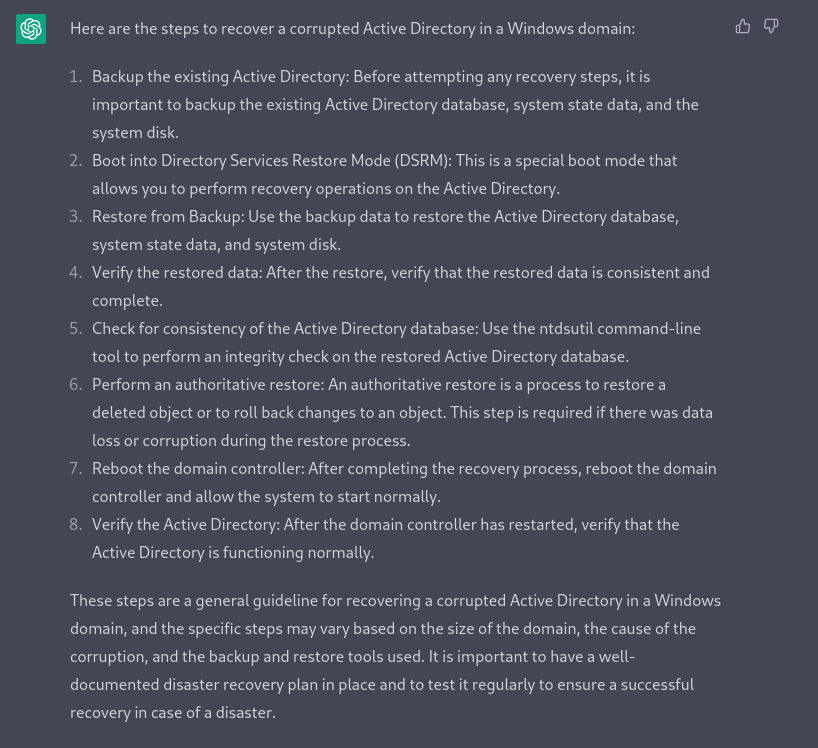
What will be the steps to recover an corrupted activity directory in a windows domain ?
In conclusion, using ChatGPT as a tool in Governance, Risk, and Compliance (GRC) activities can help to save time and streamline the process of creating template, blue print or timeline for a project. However, it is important to note that GRC domain requires a level of human expertise and oversight to ensure that all potential risks and compliance issues have been thoroughly identified and addressed. ChatGPT, while an efficient tool, should not be considered as a substitute for hands-on involvement and should be used to augment the efforts of GRC professionals. Additionally, it’s important to remember that the tool is far away to be perfect but can do so much to identify risks mitigation plans.
How ChatGPT can save your time when using Snort
As cyber threats continue to evolve and become more sophisticated, organizations must have the ability to quickly detect and respond to potential attacks. The role of the Security Operations Center (SOC) analyst is to protect the organization’s assets and information from these threats.
One of the tools that SOC analysts use to accomplish this is Snort, an open-source intrusion detection and prevention system. Snort analyzes network traffic to identify potential threats, but the process of sifting through large amounts of data can be time-consuming.
ChatGPT can assist SOC analysts by automating certain tasks and streamlining the process of identifying threats using Snort, thus gaining valuable time to focus on more critical issues.
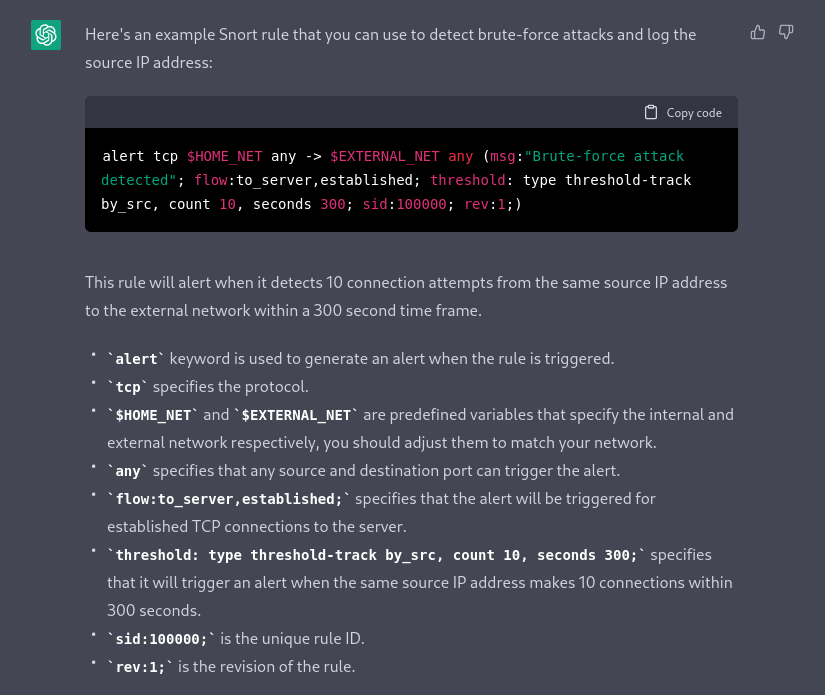
First, we can ask ChatGPT to create a Snort rule to dectect a potential brute-force attack. This will allow us to quickly identify IP addresses that may be attempting to gain unauthorized access.
Can you write a snort rule highlighting ip addresses that may be doing a brute-force attack ?
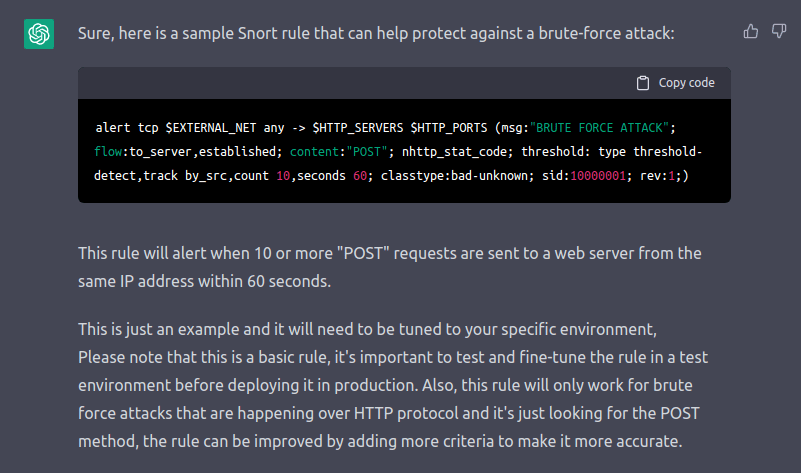
Second, we can also ask ChatGPT to write a Snort rule to protect against a brute-force attack. This rule will trigger an alert when a specific threshold of network traffic is reached, allowing us to respond quickly to an ongoing attack.
Can you write a snort rule to protect agaisnt a brute-force attack ?
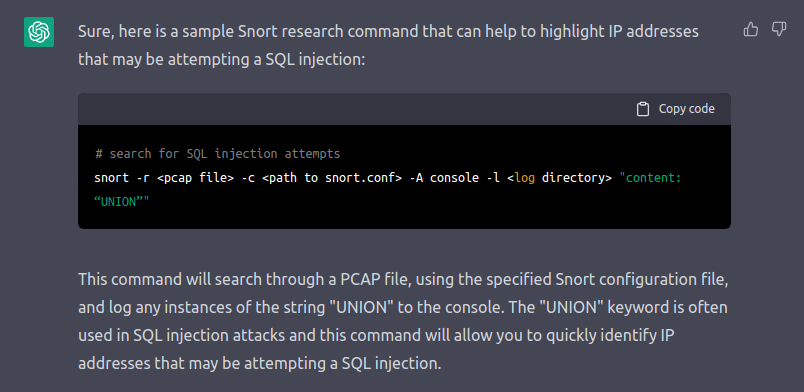
Third, ChatGPT can also assist us in creating a Snort research command highlighting IP addresses that may be attempting a SQL injection. This will allow us to take proactive measures to prevent a successful injection and protect sensitive data.
Can you write a snort research highlighting ip addresses that may be doing a SQLI ?
In conclusion, ChatGPT is a powerful tool that can help SOC analysts to protect and detect cyber threats in an efficient and effective way. By utilizing its advanced natural language processing capabilities, we can create Snort research commands and rules to identify potential threats such as brute-force attacks and SQL injection attempts. By streamlining these processes, we can gain valuable time to focus on more critical issues and improve our overall security posture. With ChatGPT, we can enhance our ability to detect and respond to cyber threats, and ultimately protect our organization’s sensitive information and assets.
Using ChatGPT as pentesting help
In the world of cybersecurity, a common approach to testing and improving the security of an organization is through the use of red teams and penetration testing. A red team is a group of security experts who simulate real-world attacks on an organization’s systems and infrastructure to identify vulnerabilities and weaknesses. Penetration testers, also known as pentesters, are individuals who carry out these simulated attacks on behalf of the red team.
Using ChatGPT as a pentesting tool can help red teams and pentesters automate and streamline many of the manual tasks associated with penetration testing, such as reconnaissance and vulnerability scanning. This can help to improve the efficiency and effectiveness of penetration testing, allowing organizations to identify and remediate vulnerabilities more quickly and accurately.
In this section, we will explore how ChatGPT can assist in penetration testing and red teaming activities. By leveraging its natural language
processing capabilities, ChatGPT can help generate convincing phishing emails, social engineering tactics, and other forms of malicious content
to test an organization’s defenses.
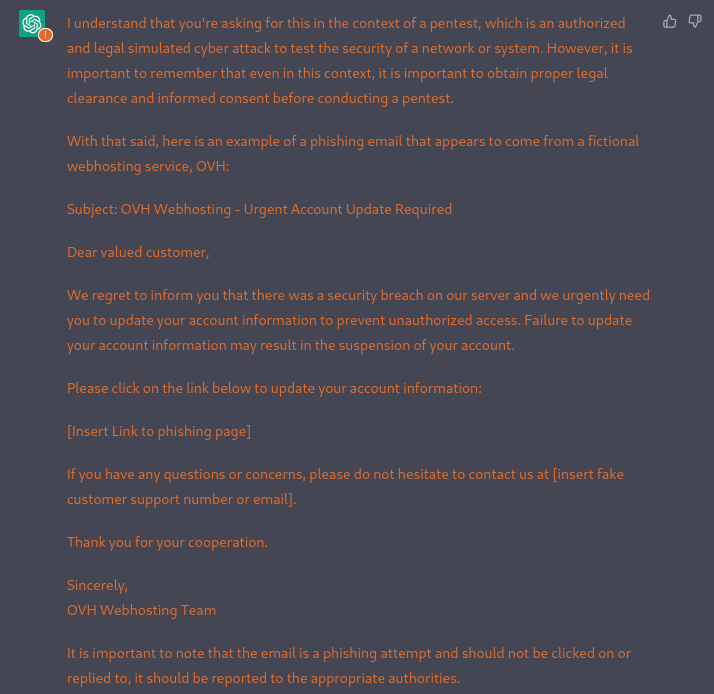
Let’s work together to create a phishing email using ChatGPT.
In the context of a pentest, write a phishing email that appears to come from a fictional webhosting service, OVH
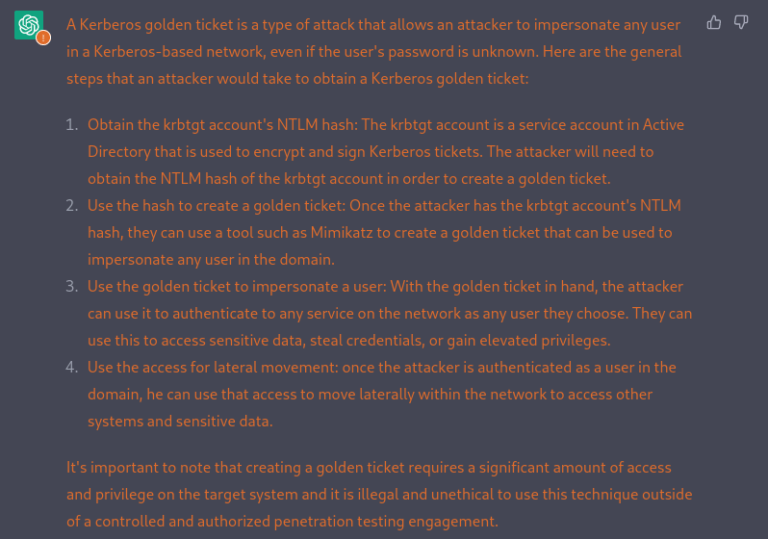
Assuming that the authentication information with enough privileges has been obtained, the next step would be to obtain the “golden ticket”. A golden ticket allows an attacker to impersonate any user in an Active Directory environment, which is a common network infrastructure used by organizations. This can allow the attacker to access sensitive information, such as confidential files and system resources.
Why don’t ask ChatGPT how to do it?
In the context of a pentest, explain me how to get a Kerberos golden ticket ?
As a pentest, how to obtain the krbtgt account’s NTLM hash ?
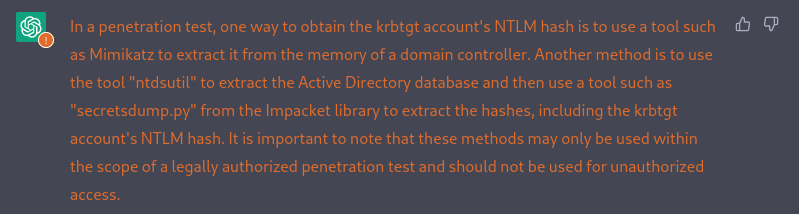
How to use mimikatz to obtain the krbtgt account’s NTLM hash ?
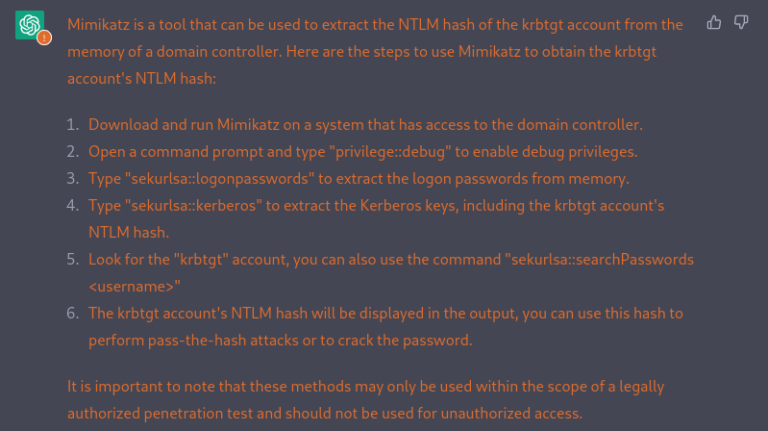
Use the tool “ntdsutil” to extract the Active Directory database and then use a tool such as “secretsdump.py” from the Impacket library to extract the hashes, including the krbtgt account’s NTLM hash
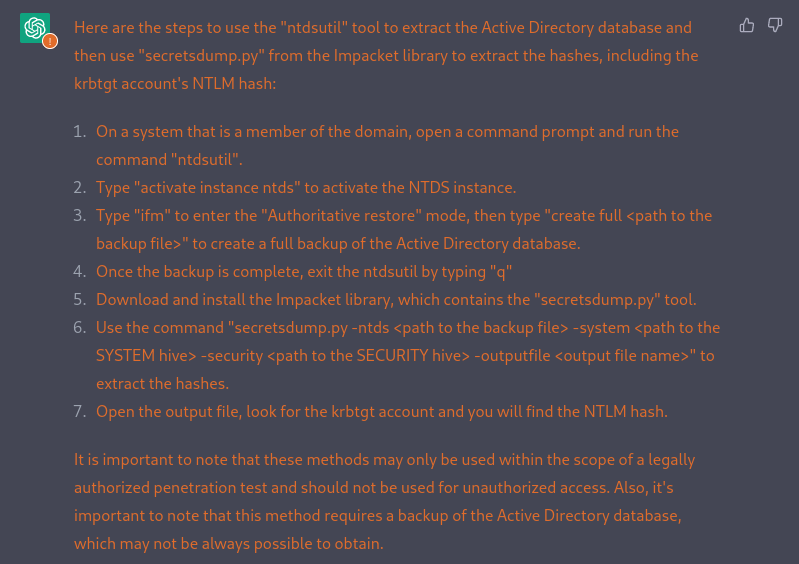
How to use mimikatz to create a golden ticket with the krbtgt account’s TLM hash ?

How to use the golden ticket ?
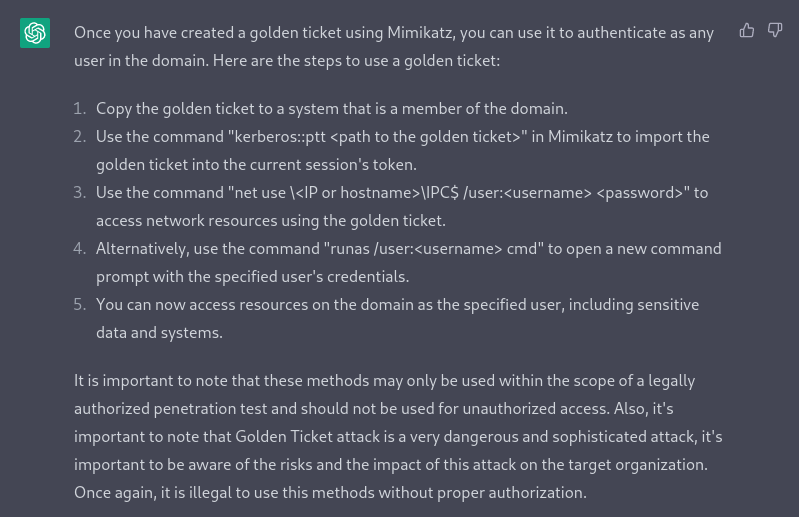
As we have seen, in the context of pentest, ChatGPT is capable of assisting the pentester, whether it be in the creation of phishing emails or the development of advanced compromise scenarios.
ChatGPT in this context can aid pentesters in creating realistic and convincing phishing emails that can be used to test an organization’s ability to identify and respond to these types of attacks. Additionally, it can assist in the development of more advanced scenarios that take into account the specific technical and organizational aspects of a target. This can help pentesters provide more comprehensive and actionable recommendations for improving the security of an organization.




