10 Tips for Protecting Yourself from Phishing Attacks
Learn how to identify and avoid phishing emails with these tips
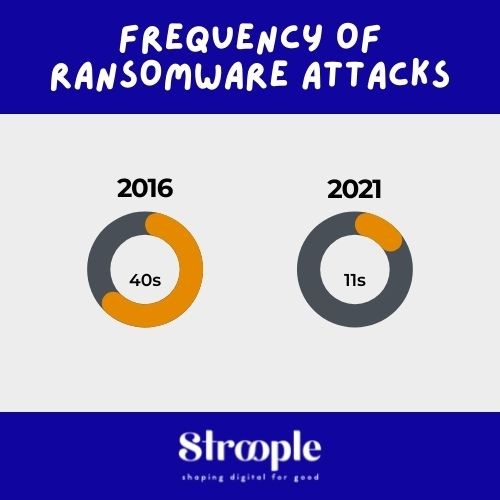
Ransomware attacks are spiraling out of control.
We live in an era of unprecedented uncertainty and ransomware attacks are spiraling out of control. Over the past 24 months, shifts in hacker tactics have resulted in a resurgence of ransomware attacks and ransomware menace currently represents the most serious computer threat to businesses and institutions. This risk is increasingly difficult to control and mitigate. With so many devices scattered throughout enterprise networks, it’s challenging for security professionals to cope with cyber security issues.
More and more cybercriminal groups are specifically targeting financially strong companies in so-called “Big Game Hunting” attacks, sometimes carried out in combination with other malicious code (banking trojans or crypto mining). These attacks are carried out by groups of attackers with significant financial resources and technical skills.
The Colonial Pipeline and Kaseya incidents and the large-scale disruptions and cost of ransomware operations, illustrate the growing impact of cyber threat activity on business risk across all industry sectors. Enterprises either pay a small amount up front by investing properly in security or much more later dealing with the effects of an attack.
What ransomware attacks are and how they occur?
Ransomware attacks put your business at risk.
Ransomware is an advanced type of malicious malware that encrypts or locks all kinds of victims’ files (videos, images, audio) that reside in their computer memories. A ransomware attack is typically delivered via an e-mail attachment which could be an executable file, an archive, or an image. Once the attachment is opened, the malware is released into the user’s system. Cybercriminals can also plant the malware on websites. When a user visits the site unknowingly, the malware is released into the system.
Some ransomwares can scramble file names so that victims won’t be able to detect which data is infected. New variants of ransomware known as CrypoDefense, CrytoLoker and CryptoWall are spreading via spam emails, drive-by downloads, or by malware already on computers. The infection is not immediately apparent to the user. The malware operates silently in the background until the system or data-locking mechanism is deployed. Then a dialogue box appears that tells the user the data has been locked and demands a ransom to unlock it again. By then it is too late to save the data through any security measures.
Research identifies two types of ransomwares: encrypting and locker ransomwares. Encrypting ransomware demands a ransom payment in exchange for the unique passkey necessary to unblock the encrypted content. The locker ransomware does not encrypt the victim’s data but it will prohibit them from having access to it until the victim pays the ransom the attacker demands.
So, to restore access to the data, the attacker demands a ransom from the victim. The victim is shown instructions for how to pay a fee to get the decryption key. Some cybercriminal groups seek to pressure their victims by disclosing internal data previously exfiltrated from the infected information system. The costs can range from a few hundred euros to tens of millions, payable to cybercriminals in cryptomoney.

Recent ransomware targets like Colonial Pipeline and the chemical distribution firm Brenntag paid the equivalent of $4.4 million to the groups that hacked them in May 2021 before they could regain access to their systems and relaunch operations.
It is possible to categorize ransomware attacks into three types: first, untargeted attack campaigns (well-known in open source like Fire and Forget or Spray and Pray) which are popular in part because they are relatively easy to execute and because, to end the breach, victims often pay, second, automated mass campaigns and third, targeted attacks called “Big Game Hunting”.
Ransomware actors test continuously new extortion methods and seek out opportunities to infect more computers. Tactics, Techniques, and Procedures (TTPs) are more and more advanced and threat actors may rapidly shift efforts, especially following any high-profile incident. They target Linux systems, operational technology (OT), IoT devices, and cloud environments.
Others, available on cybercriminal markets through an affiliate system known as “Ransomware-As-A-Service” (including Dharma, GandCrab, or Maze Sodinokibi), are used both in a targeted manner and in massive campaigns depending on the willingness and capabilities of cybercriminal groups subscribing to the service. Ransomware as a service (RaaS) is a subscription-based model that enables affiliates to use already-developed ransomware tools to execute ransomware attacks. To recruit affiliates with specific technical skills, some ransomware gangs, like AvosLocker or Circus Spider RaaS post affiliate opening on forums on the dark web. Then, affiliates earn a percentage of each successful ransom payment.
How to defend against ransomware attacks?
The cybersecurity community is facing a crisis caused by the escalating threat of high-profile ransomware attacks. Operational technology (OT) threats have the potential to lead to real-world effects: shutdown of a production plant, machinery malfunctions, chemical spills or even crashes of trains or passenger vehicles. So, how do we stop ransomwares like these? How to keep your data safe?
Good news! Here are some important countermeasures for a healthy information system to prevent a ransomware attack from affecting the organization or reduce the losses linked to such an attack.
The following simple cyber security advice can help you avoid becoming a victim of ransomware.
Keep offline copies of critical information
One of the most effective ways to prevent ransomware from wreaking havoc and blocking your sensitive data is to securely keep offline copies of vital information. That way, even if cybercriminals gain access to your computers and infect them with malware, you can wipe the system and restore your latest backup.
By staying focused on recovery methods, you ensure that your organization can move past a ransomware attack as quickly as possible without falling prey to the ransom or compromising critical information.
Not only ensuring the presence of backups but also their effectiveness through real-world testing makes a critical difference in the organization’s security. Store your backups offline. Ensure your back-up is not connected to the business network so that the attackers will not have the ability to also infect your backups via the network.
Consider cloud technologies if you haven’t done so already. The advantage over on-premises systems is that vulnerabilities in cloud-based architectures are more difficult to exploit. In addition, cloud storage solutions allow you to restore older versions of your files. This means that if the files are encrypted by ransomware, you should be able to return to an unencrypted version using cloud storage.
Follow basic cybersecurity best practices
To prevent vulnerabilities that could expose your organization to a ransomware attack, follow basic best practices such as thorough staff training on proper email hygiene against phishing tactics, beefing passwords, requiring regular password rotation, disabling administrator privileges for users of these workstations, and getting two-factor authentication (2FA) on every access point into a network. Enforce these policies programmatically and focus on preparation, prevention, and pre-encryption defense.
Furthermore, the application of the principle of defense in depth to the various elements of the information system will reduce the risk of total unavailability. This principle involves particularly zero-trust measures, segmentation of the network with zones of sensitivity and exposure of the various elements of the information system, by limiting the privileges granted to users or by controlling Internet access. Tools and protocols such as RDP (Remote Desktop Protocol) are a very common path for ransomware attacks. Disable them except where they’re absolutely necessary.
Double check your organization’s patch management structure with security and detection upgrades. Of course, patching is easier said than done. Your IT team first needs to test the patches for conflicts with existing applications and configurations. Testing could conflict with application development time. However, you must balance those considerations with the risks of delaying patches.
Stress test your organization’s incident response plan
Planning for a ransomware attack can make all the difference in how your organization responds at the critical moment. Make a security risk assessment checklist and define an incident response plan to ensure business continuity and a return to a nominal state.
Stress-test your organization’s incident response plan to develop muscle memory. If that’s not a possibility, engage or outsource an effective incident response capability for prompt response to high-impact incidents.

Stay current on cybersecurity trends
Get in front of the threat rather than react to it. As the ransomware landscape evolves, the best strategy to stay up to date on your organization’s response strategy is to stay plugged into the community.
Use Cyber Threat Intelligence (CTI) to better understand threat actor motivations and tactics and prioritize security resources. Cyber Threat Intelligence services provide information on threat actors targeting IT or OT.
Every industry has its share of risks. The year-over-year rise in industry targeting highlights the risks to all industry sectors and a need for meaningful advancements and maturity in cybersecurity programs across the board.
Keeping a permanent watch enables you to stay informed when software and hardware vulnerabilities are discovered in the services used in your entity and when patches are available. The CERT-FR website (www.cert.ssi.gouv.fr) can help you with this process.
As edge device vulnerabilities and targeting are on the rise, it is critical for organizations to start changing their security cultures from being reactive to adopting a proactive approach to security “on the edge.”
Infected... What to do next? How to react?
Apply a tourniquet immediately
Bad news! You’re infected! The first response is to prevent the propagation of ransomware to other IT equipment in the entity, it is important to isolate the infected equipment from the IS by disconnecting it immediately from the network and keep your data backup in safe and offline locations as soon as possible after making sure that it is not infected. In very serious cases, consider whether turning off your Wi-Fi, disabling any core network connections (including switches), and disconnecting from the internet might be necessary. Reset credentials, including passwords (especially for administrator and other system accounts), but verify that you are not locking yourself out of systems that are needed for recovery. The attackers will then no longer be able to control their ransomware or trigger a new wave of encryption. This will also prevent possible data exfiltration.
Set up your cyber crisis unit
This unit will be responsible for responding to the issues of the crisis by possibly establishing, Internal and external communication strategies and the elements to be provided for legal action or regulatory notification, particularly for the French Data Protection Authority (CNIL) in the event of a personal data breach. With the support of the Data Protection Officer (DPO), this unit will have to identify the level of risk generated for the persons whose data is affected by the breach and warn them accordingly (employees, customers, members, etc.). More generally, this unit will also be responsible for identifying the impact of these malfunctions on your organization’s activities and organizing the response in these fields.
If you have neither the resources nor the expertise required to deal with a security incident, you may call on service providers who specialize in responding to security incidents.
Report the incident
It is strongly recommended to file a complaint with the police or other competent authority in the event of a ransomware attack.
Then, open a log to trace the actions and events related to the incident. This document should always make it possible to inform decisionmakers on the progress of the actions undertaken.
Preserve any evidence, in coordination with the competent authorities investigating the attack: create a forensic image of affected systems (or a system snapshot), create a RAM dump of the affected systems, and preserve any net flow or other network traffic logs.
Don’t pay the ransom because there is no guarantee that the ransomware creators will give you access to your data.
Restoring systems from healthy sources
In the case of infected equipment, safely wipe the infected devices, reinstall the OS and restore the data from backups made, preferably, prior to the date the system was compromised. This is to verify that the restored data is not infected by the ransomware.
Unfortunately, in many cases, once the ransomware has been released into your device there is little you can do unless you have a backup, but all hope is not lost! It is sometimes possible to help infected victims to regain access to their encrypted files or locked systems, without having to pay.
No backup?! What can you do?
If there are no backups, you should try to decrypt the data locked by the ransomware with the best ransomware decryption tools available.
How to identify the ransomware you are infected with?
The ransom note often gives details about the type of ransomware with which the files were encrypted, but sometimes you do not have this information at hand and many extensions mark new types of encrypted ransomware for which no decryptions are available.
If you need help identifying what type of ransomware is infecting your system, you can use these two tools: Crypto Sheriff by No More ransomware or ID Ransomware by the Malwarehunter Team.
They are designed to help you define the type of ransomware affecting your device. This will enable you to check whether there is a decryption solution available as malware and ransomware are constantly evolving.
For instance, the “No More Ransom” website helps victims of ransomware retrieve their encrypted data without having to pay the criminals. This initiative is open to other public and private parties. They have created a repository of keys and applications that can decrypt data locked by different types of ransomwares. They have decryptions for Alcatraz Decryptor, 777 Ransom, Amnesia Decryptor 2, BigBobRoss, Pylocky, Thanatos, and so many more.
Some ransomware decryption tools are easy to use, while others require a little more technical knowledge.
If you don’t find the right decryption tool, it is therefore important to keep the encrypted data because an encryption solution may be discovered and made public later.
As with other forms of malware, careful action and cybersecurity awareness are a step in the right direction to cope with the menace. Of particular importance with regard to this type of malware is the creation of backups, as this allows you to be well prepared even in a worst-case scenario. We hope the previous tips will be valuable to help you move toward your information security and data protection goals.
Need help unlocking your digital potential and protect your most sensitive digital assets ?


