How to run an effective Phishing Security Test?
Would your employee know if they received a phishing email?
Businesses are breached every day and more than 90% of them begin with a phishing attack.

Did you know that more than 90% of successful data breaches started with a spear phishing attack? The first step to eliminating a problem is understanding that it exists. Phishing is a threat to every organization across the globe. Running an effective phishing test at work can be the difference between an employee who clicks on malicious links or attachments and one who reports them. Whether you’re debating the idea of running an internal phishing security test campaign or scratching your head on how to get started, this article will give you informations you need.
In this article, we will analyze the process of a phishing test, from its implementation to its reporting and how it can protect your business. We will discuss the framing, the technical deployment, the execution and the post-simulation exercise.
What is Phishing?
Would your employee know if they received a phishing email? Phishing is a form of social engineering involving the use of bait tactics to trick users into giving away personal or sensitive information via email.
We receive and hundreds of email every day. Phishing scams have become increasingly more sophisticated, and hackers employ a variety of modern and custom tactics to trick users into divulging sensitive information like usernames and passwords. And while there are many security tools that block most spam and phishing emails, ultimately, some make it through.
An organization succumbing to such an attack typically sustains severe financial losses in addition to declining market share, reputation, and consumer trust. Depending on scope, a phishing attempt might escalate into a security incident from which a business will have a difficult time recovering.
There are a number of different techniques used to obtain personal information from users. As technology becomes more advanced the hackers techniques being used are also more advanced.
To prevent Internet phishing, users should have knowledge of how hackers do this through phishing security test campaigns.
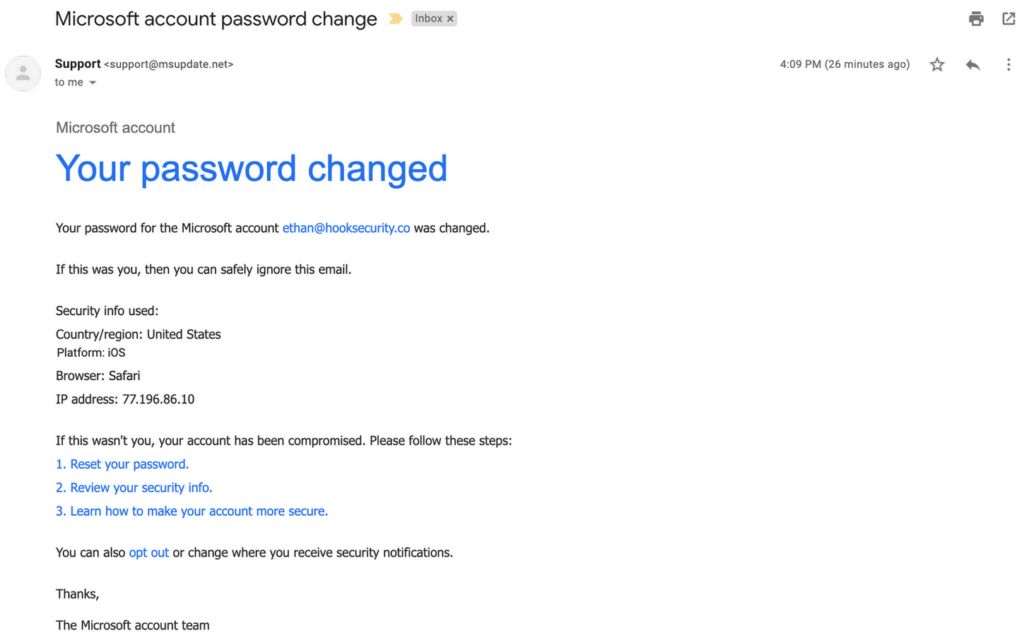
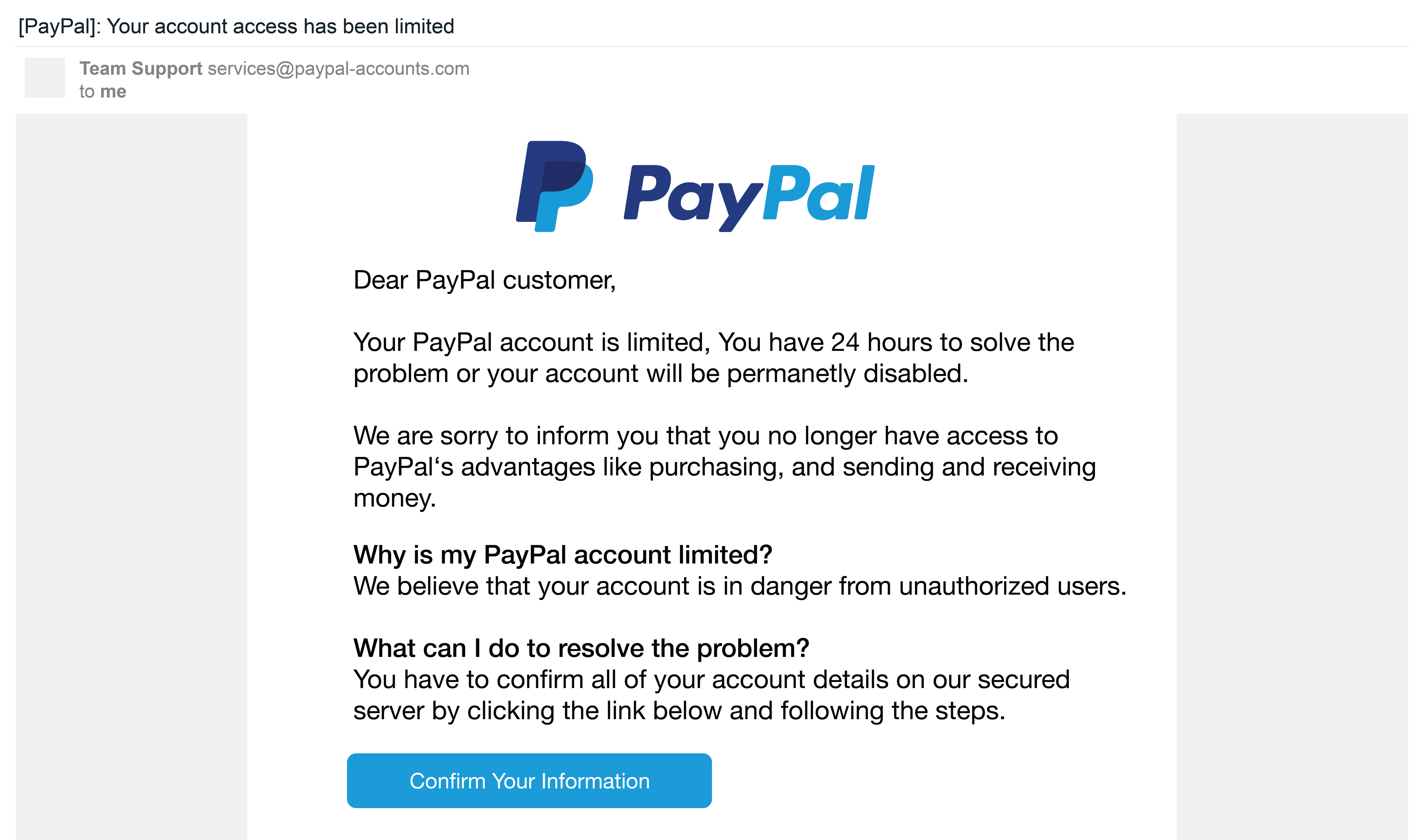
What is Phishing Security Test?
A Phishing Security Test is an online tool that tests your security and phishing vulnerability. It is used by security and IT professionals to create mock phishing emails or webpages that are then sent to employees. The phishing security works by sending an email to your users. If the user clicks the link in the PST, they will be directed to a landing page. Landing pages tell the user they failed a simulated phishing test and give them some tips for inspecting emails in their inbox.
These fake attacks help employees understand the different forms a phishing attack can take, identifying features, and to avoid clicking malicious links or leaking sensitive data in malicious forms. They get real-life experience without any of the risk. They’re also given a chance to improve their security behavior in a meaningful way with feedback from IT when necessary.
For IT and security professionals, a phishing security test can help you determine how many users in your organization may be susceptible to a phishing attack.
How do Phishing Security Tests work?
There are a few rules to follow to ensure your phishing test achieves maximum effectiveness and improves employee cybersecurity behavior in the long run.
What to do before a Phishing Security Test
Before you dive right into a phishing test, there are a few things you need to have prepared. You’ll need some data such as your target users, but most importantly, you need to set the right expectations.
Then, you’ll need to find a phishing test tool that can help you accomplish your goals.
There is a seemingly neverending list of phishing tools out there, from open source to proprietary, to simple-to-use vs highly advanced.
It’s important to find the right fit for your business by answering questions about budget, requirements, integrations.
We suggest finding a phishing tool that nails these 5 basics:
- Is used the latest attack techniques from hackers,
- Is easy-to-use,
- Has pre-loaded phishing templates,
- Is automated to facilitate ongoing simulations,
- Has great reporting.
Once you’ve chosen a phishing test tool, you can begin planning.
Planning a Phishing Security Test
Phishing simulations are often launched as part of a wider human risk management approach and are administered periodically using different techniques and messaging. In most cases, the simulation is administered by the business’s cybercurity team or cybersecurity provider and run as follows.
Timing
A test should be constructed as a series of phishing simulations – a campaign – delivered each month or each quarter. That’s the only way to gauge success and improvement.
Your campaign should be progressive in terms of difficulty – your first test should be fairly simple to identify. After that, try various angles and different levels of subtlety in your tests, as outlines in the next section.
Best practices for running a phishing campaign
A phishing campaign needs to accurately emulate the tactics and techniques that are used by real attackers, using hooks that will have the most emotional impact on the target. Hackers use a variety of different tricks to fool people, but most attacks revolve around:
- Altruism – eg. asking the recipient for a quick favor
- Reward – e.g. entering a prize draw to win a huge discount
- Hope – e.g. downloading an attachment to see who won that quarterly challenge
- Fear – e.g. notifying a password is about to expire and click a button to keep using it
- Anxiety – e.g being asked to make an urgent wire transfer by the CEO
As well as using the right tactics in your messages, it’s even more important to make sure that there is a well thought out approach for planning, delivering and tracking the ongoing simulations.
Utilize different methods of phishing to give employees multiple opportunities to learn and keep them on their toes. While the first email should be a basic phishing template, subsequent emails should utilize social engineering tactics and more devious schemes to trick the employee as a hacker would.
Inform your staff
Deploying phishing simulations without first explaining to your staff why the business is looking to run these campaigns can be a surefire way of creating an ‘us VS them’ mentality between senior management and the wider business.
Present a short training to establish what is or isn’t a phishing email, or a few tips on what to look out for, and then notify employees that you will be running phishing tests to help prepare employees for an attack in a controlled setting.
It’s important to explain why these efforts help keep the company, its employees and its customers safe, otherwise, people might feel caught out for doing something wrong, rather than finding value in learning from their mistakes in order to avoid falling victim.
You should also create a specific company email address (e.g. [email protected]) and inform your employees to forward suspicious emails to this address for IT review. Additionally, you can download a report phishing button to embed into each employee’s inbox. It’s good to encourage open communication when employees discover fishy emails.
Top management sponsorship
If you want employees to really get behind the value of running internal Phishing Security Tests, then a clear and consistent message needs to come from the top down. After all, combatting phishing attacks isn’t just a problem for the cybersecurity folks, it’s everyone’s responsibility within the business.
During a simulation campaign, keep them going
Simulations should also be continuous, not just a one-time thing – phishing attacks are constantly evolving, so continuous testing will give your employees the experience to spot even the newest and most sophisticated attacks.
Try to make sure each member of staff is receiving a phishing simulation at least once per quarter to help track risk while keeping education at a high, without going into overkill and annoying people.
After a Phishing Security Test, track the essentials
Once your campaign is complete, it’s time to tally up the scores, report the data to the necessary stakeholders, and let employees know how they did.
It’s also important to look at the key performance metrics to make sure that you’re aware of where the risk is increasing or decreasing across the organisation.
There are four key metrics you want to be measuring:
- Open rate – How many people opened the simulated phishing email
- Link click rates – How many people clicked a link in the phishing email
- Number of employees that leak sensitive data (e.g. on a fake sign-in page purporting to be their email provider) or number of employees that downloaded the ‘harmful’ attachment that could have contained ransomware (e.g. a fake invoice)
- Number of employees who reported a phishing email
The only way to show progress is to measure the impact over time and make note of these metrics after each test. You should share results with the rest of the organization.
Spotting trends and measuring ongoing results is essential for determining whether or not phishing awareness is improving. This should involve comparing results from multiple campaigns over time to see how many users are being compromised in simulations compared to previous months.
Educate and reward
Since your goal is to improve cybersecurity awareness among employees, your job has only just begun.
During your early phishing campaigns, it’s highly likely that at least some users will become compromised, with some businesses even seeing more than one-third of their staff take the bait in an early phish.
Any phishing simulation should be positive and transparent. Phishing is on the rise, and it only takes one unsuspecting person to expose an entire organisation.
Build a baseline, reward high-performers but don´t name and shame users who fail a phishing simulation, educate them and start planning your next test!
Some phishing training programs experiment with the idea of letting workers design their own attacks. It begins with a task to scan for public information, available on the internet, about a company. The team running the training then selects a set of submissions and sends the employee-generated phishing emails to other people in the organisation. They then measure the different campaigns against each other and announce which ones performed better.
Employees can learn a lot about phishing attacks by trying to imitate how deceitful minds work and become aware of what type of public information can be easily weaponised for targeting specific people or departments. For example, they can see how social network posts can make companies vulnerable.
These types of activities are complementary to standard and automated phishing tests. They illustrate how keeping up with malicious threats can be an evolving challenge – but also a chance to engage in team-building activities that fight cybercrime.
By following the guidance outlined here, you’ve laid the groundwork for what is sure to be a successful and rewarding program that helps limit the attack surface of your organization and keeps your employees safe from malicious outsiders.
What’s next? Start preparing for your next phishing test!
Phishing awareness and continued testing is necessary as your company grows and as phishing methods evolve. Phishing simulations are a bit like a phishing vaccine: to develop immunity to a virus, you administer a vaccine – a small dose of the virus – to teach the body how to combat it. To defend against phishing, you administer phishing simulations to teach your employees how to combat the threat.
Although phishing tests can be helpful to protect users, using questionable tactics has the potential for harming relationships between a company and its employees. As a security awareness professional, we advocate for the importance of the human element. Cybersecurity is not (just) a tech issue. We suggest that security teams should avoid this damage by employing phishing tests with three criteria: Test teams, not individuals; don’t embarrass anyone; and don’t punish but reward.
We hope this article helps you accomplish peak employee cybersecurity awareness so you can rest easy knowing employees won’t be scammed into clicking on the next phishing link to come through their inbox.


