Back in 2016, following increased concern over the threat of cyberattacks, the EU launched the first piece of EU-wide cybersecurity legislation – the Network and Information Systems (NIS) Directive. The NIS Directive (NISD) aimed to ensure a certain level of security for networks and information systems belonging to critical and sensitive infrastructures in EU member states.
The NISD soon began to show its age. Cyberattacks and data breaches have increased exponentially since 2016, specifically as people become more reliant on digital technology. The increase of cyberattacks year over year revealed the limitations of the previous model and the urgent need to adopt a new one.
The newly named NIS 2 Directive, adopted in January 2023, is an updated EU cybersecurity law that builds on the original NISD. The goals of NIS2 are to enhance cybersecurity, simplify reporting and create fixed standards and penalties across the EU.
By expanding its scope, NIS2 brings into scope more sectors to take cybersecurity measures, with the ultimate goal of boosting Europe’s cybersecurity in the long run. With stricter rules to overcome previous limitations, NIS2 impacts a wider range of industries. Member states have until October 2024 to complete the transposition and ensure their organisations are impacted by NIS2.
Organizations should start preparing by defining their compliance roadmap and optimizing their cybersecurity awareness.
Does NIS 2 apply to your business?
The scope of NIS2 is much wider than the previous legislation, with more businesses and organisations coming under the remit.
NIS2 now provides an extended and comprehensive list of 11 sectors that fall under “essential services”, and an additional 7 sectors are marked as “important services,” also subject to regulation.
However, the directive also applies to medium and large organisations (defined by the EU as those which employ more than 50 people and whose annual turnover exceeds €10 million).
NIS 2 Scope expansion
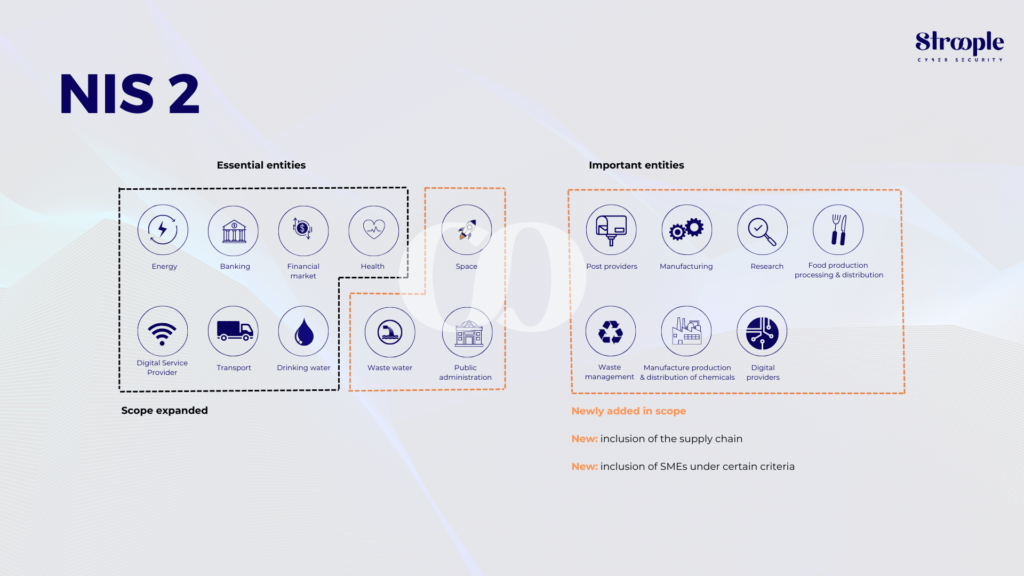
Smaller organisations who are also critical to the member state’s functioning are also included in this remit due to the potential problems that could arise if they were hit by a cyberattack.
Additionally, in each sector, operators are required to verify compliance of their supply chain.
This means that even if your organisation does not fit into one of the types of entities, if your customers or prospects are on this list, they may require you to comply with NIS2. You not be supervised by the national authorities regarding NIS2, but by your customer. So, even if your organization is not in scope, it is wise to maintain customer trust and stay competitive by demonstrating compliance both before the transposition and from the start. So, what key measures should the affected organisation take to?
What are the core requirements of the NIS 2 Directive?
The next, more substantive change brought by the new Directive is a list of 10 cybersecurity measures that will need to be implemented in every organisation and business that falls under the scope of NIS2. This list can be found under Article 21(2).

Perform Risk Analysis
A critical part of cybersecurity is assessing your risk level. NIS 2 will require companies to evaluate the potential impact of an attack on their most vital assets.
Ensure Business continuity
No matter how effective the countermeasures, incidents are inevitable, whether due to equipment or communications failure or from a breach—perhaps using some previously unencountered attack vector. When this happens, you must have a verifiable plan for how your company will react to an attack and how it can recover from it as quickly as possible, minimising disruption. As a result, NIS 2 includes a focus on cloud backup solutions.
Focus on key supply chains
Recent incidents all over the world have proven the importance of continuity within critical supply chains, which is why NIS2 ensures that organisations clearly understand the risks, maintain a close relationship with suppliers, and continually update security to guarantee the highest possible protections.
Vulnerability Disclosure
NIS2 requires transparent vulnerability disclosure and management. This means, for example, that if your organisation identifies a vulnerability within your network, it must disclose it to make sure the vulnerability is not exploited elsewhere. Disclosure of such vulnerabilities will support the fight against cybercrime and ensure they are not exploited elsewhere.
Incident Reporting
NIS2 has designed a new timeline for reporting incidents. Every incident with significant impact should be notified by the essential and important entities without undue delay.
An incident is considered significant if it:
- has caused or is capable of causing severe operational disruption of the services or financial loss for the entity concerned;
- or has affected or is capable of affecting other natural or legal persons by causing considerable material or non-material damage.
The approach to the reporting of significant incidents is three-staged:
- within 24 hours after first becoming aware of an incident, affected companies have to submit an initial report containing some basic information about the incident (e.g. whether the incident is suspected of being caused unlawfully or maliciously);
- within 72 hours after first becoming aware of the incident, organisations should update the early warning with a more comprehensive incident notification;
- and a final detailed report should be submitted no later than one month after the incident notification including a detailed description of the incident, its severity and consequences, the type of threat or cause likely to have led to the incident and applied and ongoing mitigation measures.
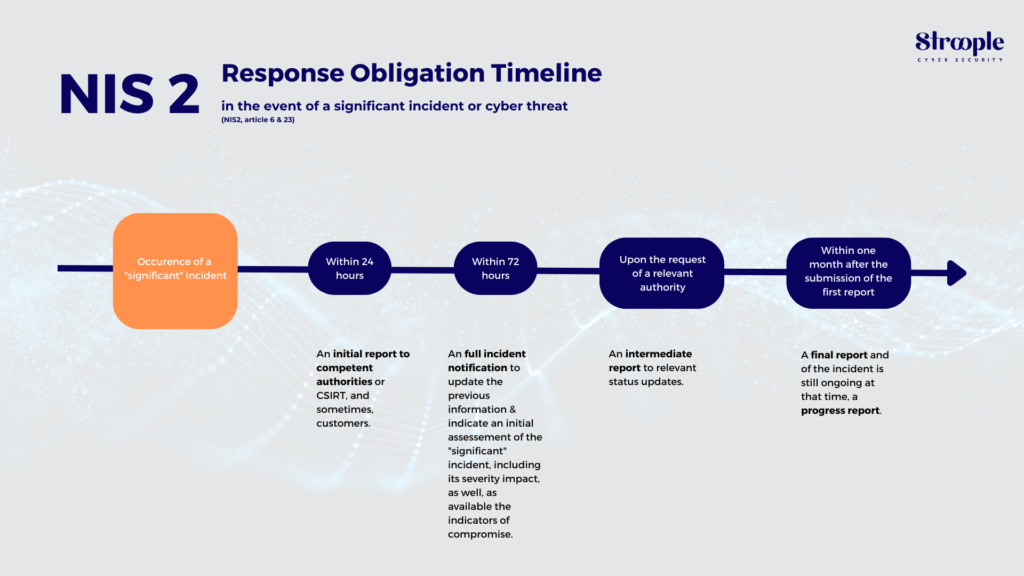
To ensure an ability to comply with these tight requirements, your organisation should start to review their internal incident response plans and incident management procedures and should consider whether they have sufficient resources and contingency in place to meet the stipulated timeframes.
What are the implications if you don't follow the NIS 2 directive?
As cybersecurity becomes such a key issue, the EU is pushing for urgent action across its member states to ensure resilience. NIS 2 introduces stricter enforcement requirements than its predecessor, including fines of €10 million or 2% of the organisation’s total worldwide turnover – whichever of these numbers are higher.
Notably, these fines are the same as those imposed for GDPR violations. The NIS 2 initiative represents a significant leap in cybersecurity and simply: it cannot be ignored.
What do you need to do to prepare for NIS2?
Based on our lessons learned from NIS, the key aspects your organization should consider the following key aspects to be on the right track for NIS2 compliance.
Stop waiting, start preparing.
The NISD2 implies a rather significant transition for most entities falling under NIS2, which can often take 1 or 3 years. Timely preparation is a key element in an organization’s journey towards compliance. Conducting a risk assessment to identify critical network and information systems, designating responsible individuals, implementing robust cybersecurity measures, getting top management support, stakeholders’ buy-in and required budget and resources will take time. Anticipate the delays and commit to strict planning with hard deadlines.
Choose a pragmatic approach to your cyber security
We like to take a more pragmatic approach to reducing cyber security risks for our clients, by using the Critical Security Controls from the Centre for Internet Security (CIS Controls). The CIS Critical Security Controls are a prescriptive, prioritized, and simplified set of best practices that you can use to strengthen your cybersecurity posture. These are a concise, prioritised set of recommendations that are based on combating real attacks that have hit businesses. The CIS Controls consist of safeguards that each require you to do one thing. This simplified cybersecurity approach is proven to help you defend against today’s top threats. There are twenty controls, each of which contain a number of recommendations. Implementing the controls significantly reduces the risk of a cyber attack.
The first five controls can be summarised as follows:
- Inventory authorised and unauthorised devices,
- Inventory authorised and unauthorised software,
- Secure configurations for hardware and software on mobile devices, laptops, workstations and servers,
- Continuous vulnerability assessment and remediation,
- Controlled use of administrative privileges.
Whilst the first five controls are regarded as essential we look at all twenty controls and map CIS Controls to NIS2 requirements when performing an independent security review for a client. Our clients get a clear idea of their areas of risk, and prioritised recommendations on measures they can take that will have the greatest impact in reducing those risks.
CIS controls are a valid place to start in order to gain an idea of your cybersecurity maturity and assess where your organisation stands in terms of relevant controls. By implementing the CIS Controls, you create an on-ramp to comply with NIS2, PCI DSS, HIPAA, GDPR, and other industry regulations.
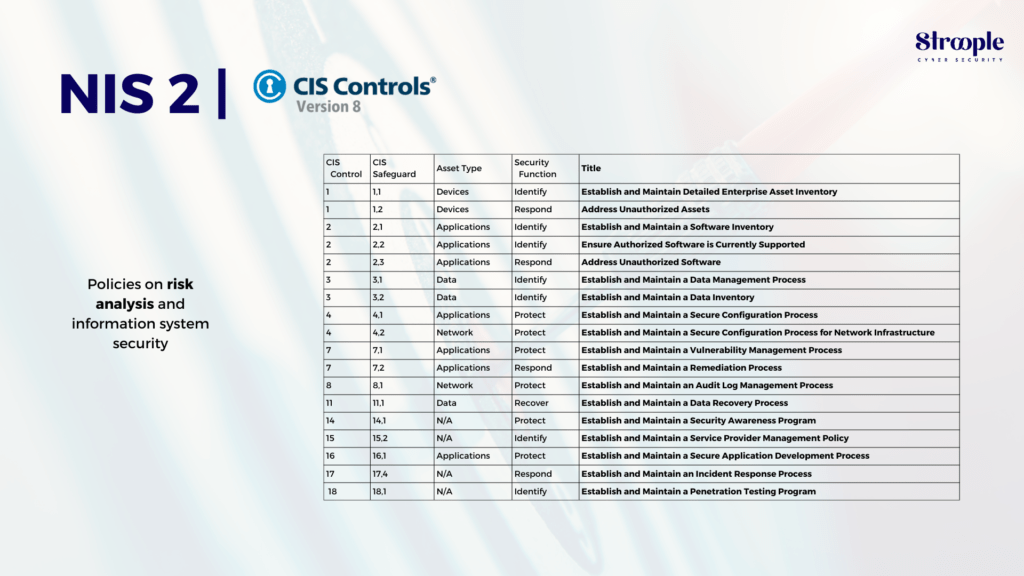
The table below maps the NIS2 measures to the CIS security controls v8 regarding policies on risk analysis and IS security.
Don't wait and act now to achieve NIS2 Directive compliance and strengthen your cybersecurity
The NIS2 Directive is a crucial piece of legislation that aims to enhance the cybersecurity of essential and important services and digital infrastructure in the European Union.
As national cybersecurity agencies like ANSSI and authorities work on incorporating the NIS2 Directive into their respective laws, companies must take proactive measures to assess and address their cybersecurity needs. Waiting for the complete implementation of the directive might put your organization at risk.
Preparing for NIS2 Directive compliance is not just a regulatory requirement but an opportunity to assess your capabilities and operations against strengthened cyber security requirements. It’s also a wake-up call on the need to act to better address cyber security threats to your infrastructure.
Therefore, it is crucial that the appropriate steps are taken as soon as possible. That the reason why Stroople has created an easy-to-use assessment tool, mapping CIS Controls to NIS2 requirements.
Indeed, CIS controls are a good starting point to get an idea of the state of your company’s cybersecurity maturity and from there to help prepare your organisation in advance to the NIS2’s member state adaptation.
Our team of experts is there to guide and assist you in your journey for NIS2. Stroople can help you assess your cybersecurity maturity, define your roadmap to compliance, identify your scope, set up and implement your risk and security management frameworks and in fine secure your business.


