Phishing, which has long been neglected, is now at the heart of everyone’s mind and has been able to renew itself in recent years, both on the attacking and defending sides.
Methods are evolving rapidly, as are the tools used to fight it. In recent years, we have seen solutions move from classic Bayesian filters (that evaluate the header and content of an incoming e-mail message and determine the probability that is constitutes spam) to so-called artificial intelligence solutions, without any massive changes in terms of processing time. In fact, the explosion of phishing usage combined with the obligation of companies to reimburse has led to an ever-increasing amount of work for the #blueteam, both in detection and remediation (through take-downs for example).
Threat hunting is something we know about at Stroople, and that’s why I’m going to present you with a simple but not very well known method that is particularly effective against security systems based on the “quality” of the domain present in the URL. Quality measured by calculating the domain seniority, domain Domain Authority and so on.
But what is Open Redirect?
The Open Redirect, we often meet it when we talk about the Web, during an audit or a #pentest. Very often, it is caused by a lack of sanitization so it is often the case that the same parameter is vulnerable to an #xss, or even #lfi / #rfi or even an #xxe.
Often considered as a minor problem in terms of pure security, the last years have shown that it can be a major problem in terms of #seo and #phishing.
Let’s skip SEO for this article even if there is a lot to say and let’s focus on the case of phishing.
Let me give you a simple definition:
An Open Redirect is an unintended redirect, without user interaction, from site A to site B.
And because nothing beats an example, I’ll give you an OR I found recently:
So if you take this link, and click on it, you will be redirected to the google site without your consent, when you were supposed to click on a civil aviation link. That’s what an Open Redirect is.
Imagine receiving for instance a email from a business you trust, sending you an amazing offer for being a customer. Because the offer sounds too good to be true, you suspect that something might be “phishy,” which is why you hover your cursor over the link to check its legitimacy.
Everything looks fine, so you click on the link. 😱 But what if the link points to the trusted website and then redirects you to a malicious webpage or application controlled by scammers? That’s exactly what Open Redirect can do.
Concret now. Open Redirect & Phishing
I think you should see now where I am going with this. With an OR, with a respectable, credible site with real activity as site A and a malicious, recent, clearly phishing site as site B, you can manage to evade.
If, for example, you were thinking of setting up a domain seniority system to fight against spam and phishing, you should also check the method. Indeed, if you classically retrieve the value of the domain in a OR case, the extracted domain will be domain A and not the malicious domain B.
Now a little practice. This time, I propose to take another example than the one above with a real phishing page. And I will use an ongoing campaign to be in real condition. Here is the phishing page once you are on it:
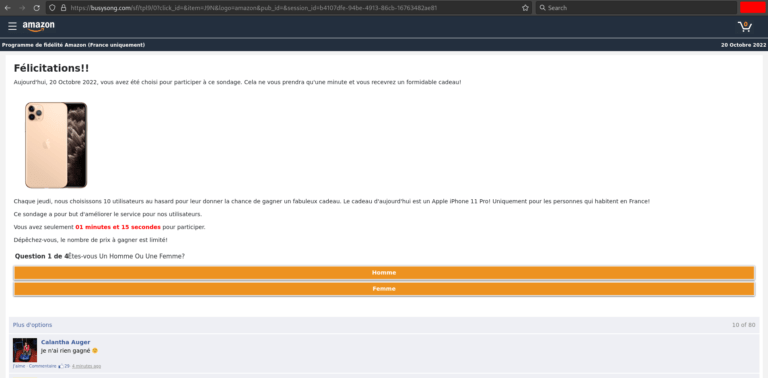
So we can clearly see that this is a phishing page, with Amazon colors because I chose Amazon via the GET logo parameter. This campaign does not only target Amazon but also French groups.
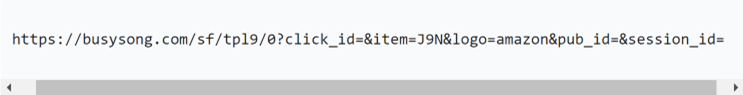
For security reasons, I will put the malicious urls in code tags so that they are not clickable. The url of the page is thus:
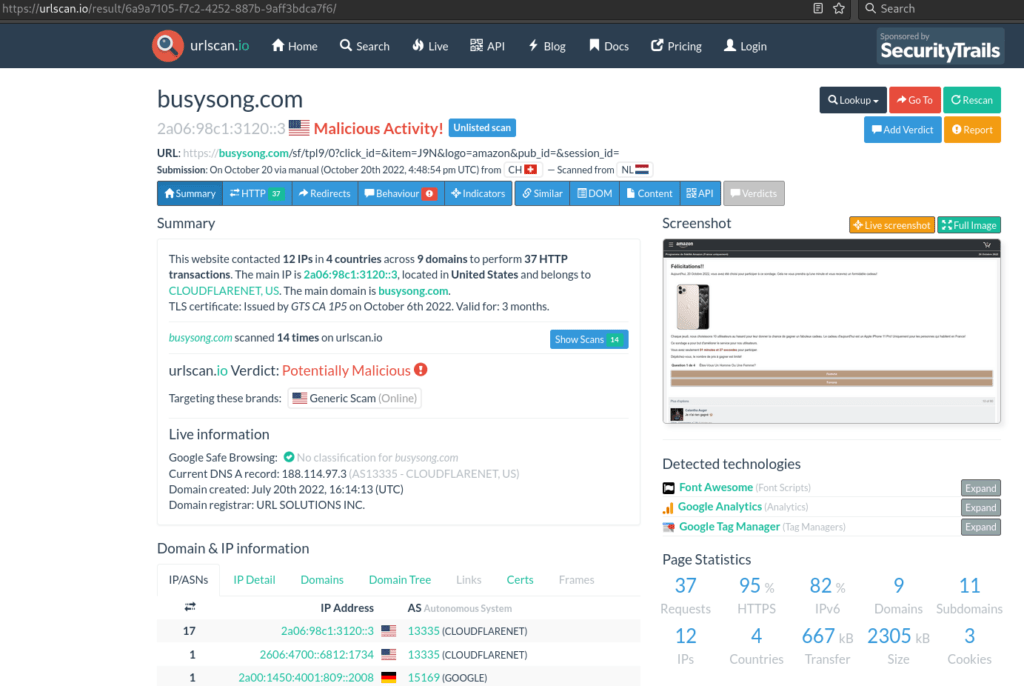
I have of course tested it on urlscan.io: https://urlscan.io/result/6a9a7105-f7c2-4252-887b-9aff3bdca7f6/
And I tested it on https://www.isitphishing.ai of Vade:
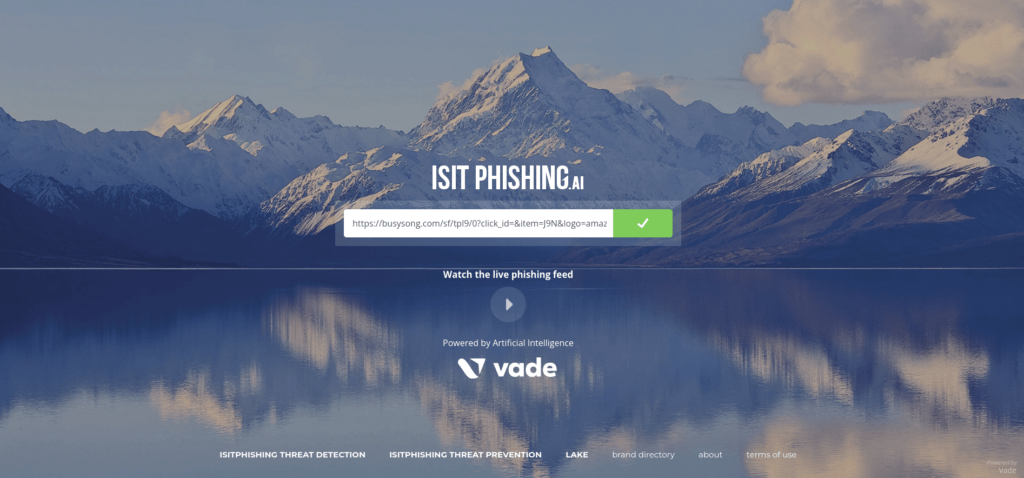
It is not yet detected by this solution but the overall idea is done. So we have an obvious phishing page with a malicious domain.
Now let’s take an OR used by an ongoing phishing campaign, and use the phishing url given above.
You will see the redirection.
To finalize the demonstration, I propose a small experiment using the urllib library to retrieve the domain value:
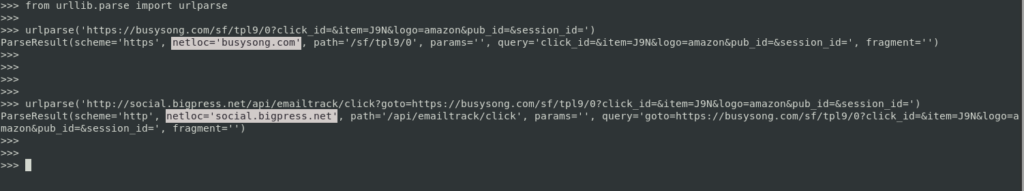
These 2 links both point to the phishing page but in the 2nd case, the OR makes the parsing consider the domain of the url as being the one of bigpress and not the destination domain which is buysong.
Of course, it is possible to further improve this method, by combining it with other methods, or by disguising the link in an html tag.
At Stroople, we know the OR well and we cover many detection methods thanks to our #cti pole. We also drive our commercial sales crazy with the OR.
Have fun and good phishing to all 😉